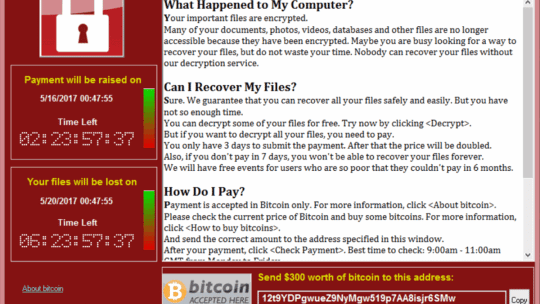
A ransomware attack ravaged the globe May 12 in the form of WannaCry, a program that spread itself through a Windows networking protocol. There was a patch, but that was no help to the countless users who had not updated and installed it.
There are many organizations that were still running infrastructure on Windows XP, a near-decades-old—and now unsupported—operating system. Microsoft offered free updates to Windows 10, but in many cases once XP was entrenched it could not easily be updated across an entire organization without entailing significant downtime, hardware updates, IT costs, etc.
Much of the blame for the crisis has fallen on Microsoft, the sentiment being that it had made a practice of pushing out incomplete and buggy products under the impression that it could simply patch problems and update operating systems as problems arose. But this does not square with the real-world behavior of users who are unable to update their operating systems or simply drag their feet, and the collision of those two factors caused disaster.
In PR News' Crisis Management Guidebook, vol. 8, Liz Zarins, an assistant account executive at 5W Public Relations, offers the following tips for moving forward after you're experienced a security breach—but in this case, use Microsoft's crisis in lieu of a crisis of your own as a catalyst to make these improvements:
- Review the organization’s cyber security efforts. Perform routine security assessments, update software regularly and enforce strict online regulations for all company associates.
- Increase internal training. Educate employees on phishing scams and other mistakes that can lead to a breach, increase IT’s security training by offering online tutorials and other free resources and practice response methods through security breach drills.
- Place more value on internal communication. Bring in communication specialists or use internal PR professionals to heighten internal communication between all employee levels, especially between executives and the IT team. Frequent communication between the two teams minimizes the opportunity for something to go unnoticed.
- Reassess your crisis plan. Plan to reevaluate your organization’s crisis plan to respond to a security breach every six months to a year. Take time to add security capabilities and communications tactics, remove outdated protection systems and incorporate lessons learned from other organizations' breaches.
Follow Ian on Twitter: @ianwright0101
